I hope the company doesn’t get offended whatsoever but, if we can find it anyone can. We were initially told that the contents of this device were confidential but, as we can see by this Crystal Disk Info result, the drive information is available to anyone:
The SSD in use is a SanDisk X600 2TB SATA SSD which is based on SanDisk’s own 64-layer 3D NAND Flash memory. There is a healthy array of available SMART attributes available to monitor this SSD and we can also see that, thus far, we have achieved 47GB of Host Reads and Writes. We were curious as to what performance we could achieve, considering all data travel is subject to encryption and decryption on-the-fly.
ATTO Disk Benchmark is perhaps one of the oldest benchmarks going and is definitely the main staple for manufacturer performance specifications. ATTO uses RAW or compressible data and, for our benchmarks, we use a set length of 256mb and test both the read and write performance of various transfer sizes ranging from 0.5 to 8192kb. Manufacturers prefer this method of testing as it deals with raw (compressible) data rather than random (includes incompressible data) which, although more realistic, results in lower performance results.
Read and write performance in excess of 350MB/s for the Aegis Fortress L3 2TB SSD is very impressive, remembering of course, that this speed is achieved through use of the USB 3.1 to USB Type-C adapter. Let’s take a look at what we might see with a straight USB 3.1 SuperSpeed connection
It is very surprising that we achieve better performance from USB 3.1 than we do with the Type-C connection. Both results are excellent results considering this is a bus-powered device and all data is encrypted or decrypted on-the-fly, remembering of course that this is SSD performance tied into Apricorns latest encryption chipset which provides throughput increases of up to 180% for read and 150% for write performance. The hard drive versions will be limited by the HDD throughput specs. Lets tackle a few more performance results on the next page.
 The SSD Review The Worlds Dedicated SSD Education and Review Resource |
The SSD Review The Worlds Dedicated SSD Education and Review Resource | 
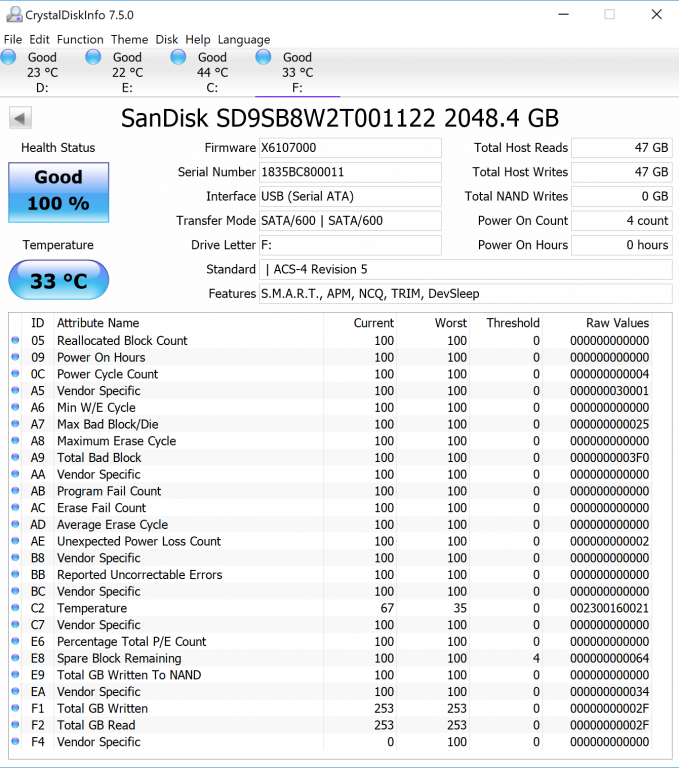

One thing it lacks is physical security.
Page 18 of the User Manual says:
Performing a Complete Reset
NOTE: A complete reset will erase encryption keys and PINs and leave the Aegis Fortress
in an unformatted condition.
There may be circumstances (forgotten PIN, redeployment, return to factory default
settings) when you need to completely reset the drive. The complete reset feature will
perform a crypto-erase on the drive, generate a new encryption key, delete all users, and
return all of the settings to factory default.
To perform a complete reset of the drive, perform the following:
1. Press and hold ? + ? + 2 together for several seconds. The RED and BLUE LEDs
will blink alternately.
2. Release all buttons when the GREEN and RED LEDs glow steadily which will
continue for several seconds, followed by the GREEN LED glowing steadily for
several seconds, and then will be followed finally by the GREEN and BLUE LEDs
glowing steadily, indicating that the reset is complete.
3. A new Admin PIN will need to be entered and the drive will need to be reformatted.
So you can steal it, erase it, reset it, and use it as if you had purchased it yourself (minus the Warranty).
we actually talk about this now and then. and yeah that’s true. and it’s true for most other manufacturers who don’t have a device management console or a software component. we thought about it a lot and opted to stick with a non managed system to allow us to lock down the firmware and eliminate update opportunities because that’s a malware vulnerability occurs and also, it’s hackable. the real concern that we focus on is the security of your data on the drive. when the average data breach cost gets up over 3 million in damages and fines, we figure you’d rather be out a few hundred bucks in the loss of the drive itself and get another one.
Thank you for jumping in Apricorn.
Couldn’t the first key entered be the ‘user lock’ for the drive, unneeded until next time a complete reset is performed?
After a complete reset one would have to enter the first key ever used, otherwise it would be a brick.
Another method would be a peel-off sticker unrelated to the serial number which contains the key to use.
Some of the drives are more than a few hundred dollars and while some might steal it thinking it had value those in the know would understand that the only “value” would be to cause concern and deprive the user of the data (which could cost thousands of dollars).
It’s like leaving your vehicle unlocked so the thief doesn’t confront you in the parking lot and take your keys – instead all vehicles have locks (some encrypted) and most people lock their cars, car jackings are infrequent (plus there’s OnStar and LoJack, no suggestion that you add it).
Thanks for answering, all the same.